Best Word List For Fern Wifi Cracker Kali
These days, there are a lot of different tools that supposedly perform the same function. This couldn’t be truer of Kali Linux, which is loaded with different tools that will help people networks. The only problem for novitiate hackers is awareness. There are many would-be hackers and security enthusiast that can’t hack Wi-Fi networks simply because they don’t know what software to use.
Aircrak-ng Aircrack-ng is perhaps one of the most widely known and utilized wireless cracking tools for Linux. Using this sophisticated yet intuitive software, even novices can learn WEP, WPA, and WPA2 security protocols. It’s less of a program and really more of a suite of useful software that helps security professionals capture packets to break the handshaking protocol, bump devices from the wireless network to force them to reconnect (to facilitate and attack), perform dictionary and brute force attacks, and even inject packets into a wireless system.
However, Akiko is more upset that her father is not able to attend the wedding and demands to know why he even became a Kamen Rider in the first place. Kamen rider w sub indo mp4 movies.
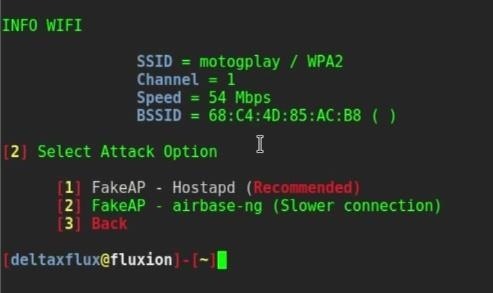
Within this suite of software, there are tools for the following: • Cracking wireless passwords (aircrack-ng) • Generating traffic to de-authenticate connected wireless clients (aireplay-ng) • Capture wireless packets (airodump-ng) • Create fake access points (airbase-ng) This software comes standard in the Kali Linux package, assuming that you choose to include the package in the installation process. If not, it can be downloaded and installed for free. The only caveat is that your wireless card needs to have packet injection functionality. Reaver Next is Reaver, which is nearly as popular as aircrack-ng. It is a highly sophisticated tool that is aimed at breaking Wi-Fi Protected Setup (WPS).
Become a Patron and Donate Just $2 To Support Us. Best Hacking Laptops & PC 1. Alienware AW17R4-7352SLV-PUS 17' QHD Lapt.
Not only can it perform brute force password attacks, but it can also recover PINs for the WPA/WPA2 security algorithms. Believe it or not, most wireless devices in a home environment have WPS enabled by default, making Reaver incredibly practical. It’s not perfect, though. Patience is a virtue, and Reaver can typically crack a wireless router in 5 to 10 hours.
The length of time depends on a variety of factors including password strength, wireless signal strength, and distance to the access point. Pixiewps Though less famous than the preceding two tools, PixieWPS also targets WPS security flaws.
Like Reaver, it leverages brute force attacks against WPS PINs to crack wireless networks, aptly named a pixie dust attack. In the scope of security tools, PixieWPS is relatively young, but it has garnered so much popularity that it deserves an honorable mention. Wifite Wifite is yet another great tool to crack wireless networks using WEP, WPA, WPA2, and WPS algorithms.
However, there are a lot of different parameters to setup before a user can begin using the software. Although, like aircrack-ng, Wifite will do all the heavy lifting for you, making the attack process ludicrously simple. In fact, many would agree that the most tedious part of the process is setting up the software. Not only can it capture the algorithms’ handshakes and de-authenticate connected users, but it can also spoof an attacker’s MAC address. Wireshark Wireshark isn’t purely a wireless cracking tool per se. In fact, it is really a full featured packet sniffer that can be used on all of the major operating systems. Using this tool, users can capture data straight from the wire or grab wireless packets out of the air.
As such, it is an extremely useful tool for those wishing to analyze and crack wireless networks. Though it is probably too advanced for novices to understand everything they are seeing in Wireshark, it is a handy way to see each and every packet that is being transmitted. In addition, it has handy filtering features that allow an attacker to sift through different protocol data to analyze a user’s activities. Lastly, it is available on most major operating system platforms, and there is a GUI as well as a Linux command line interface. OclHashCat Though it isn’t included in Kali Linux by default, it can capture handshakes and perform a variety of password attacks including dictionary and brute force. One of the real benefits of this tool is that an attacker can use their GPU cycles instead of their CPU to crack a password, thereby offloading the majority of the work and speeding up their local machine. However, it is only available for Linux and Windows, and there are some constraints regarding which GPU’s can be used, such as AMD and Nvidia cards.
Productivity Software Drivers. Apply Filters. Results for magicscan. Update your Umax MagicScan scanner software to work with the new PowerMac G3 machine. Free User rating.  Choose a proper version according to your system information and click download button to quickly download the needed driver. Driver Talent. Driver Talent. Magicscan Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on 4/6/2019, downloaded 1395 times, receiving a 79/100 rating by 1119 users. Most Popular Drivers 1. Latest Version Driver Purchase, Please Request By Email. Looking for whole range of Magicscan Scanner?Welcome to visit www.magicscan.com.my sales@lcm.com.my +603. Use the links on this page to download the latest version of MagicScan drivers. All drivers available for download have been scanned by antivirus program.
Choose a proper version according to your system information and click download button to quickly download the needed driver. Driver Talent. Driver Talent. Magicscan Driver for Windows 7 32 bit, Windows 7 64 bit, Windows 10, 8, XP. Uploaded on 4/6/2019, downloaded 1395 times, receiving a 79/100 rating by 1119 users. Most Popular Drivers 1. Latest Version Driver Purchase, Please Request By Email. Looking for whole range of Magicscan Scanner?Welcome to visit www.magicscan.com.my sales@lcm.com.my +603. Use the links on this page to download the latest version of MagicScan drivers. All drivers available for download have been scanned by antivirus program.